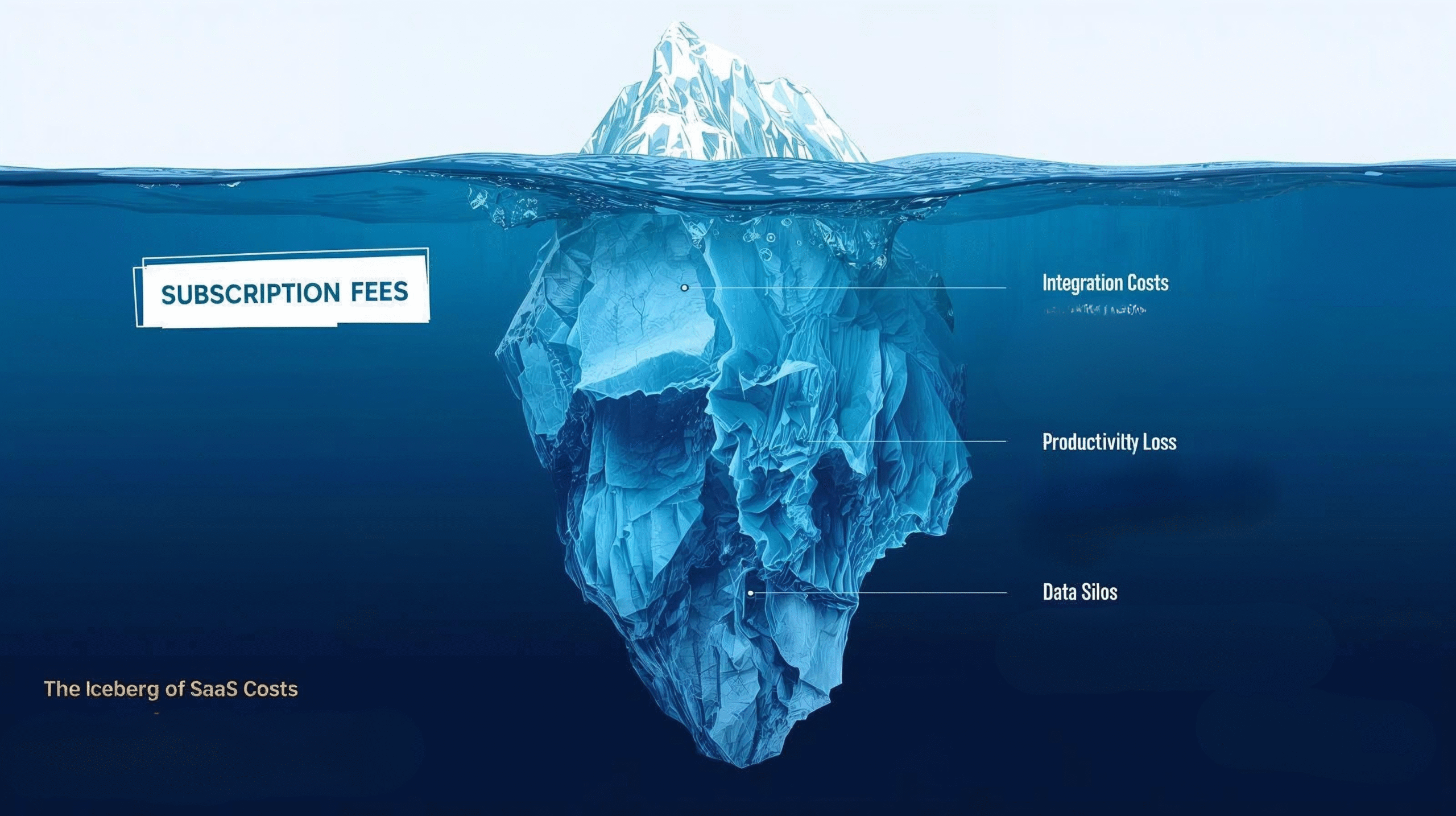
Look, I guess we all know the drill. We start small, right? A subscription here for marketing, another one there for dev operations, and suddenly, SaaS Audit Checklist? That sounds like something you do when the finance team finally screams. And it’s not wrong. But honestly, if I had to bet, the real value in running a proper SaaS audit checklist isn’t just cutting 500 a month from some unused license. It’s about not letting your operational “messiness” become a genuine, massive security risk. That’s the kicker.
The greatest liability in the modern enterprise isn’t a faulty piece of technology; it’s the forgotten subscription, the redundant platform, and the underutilized tool. A strategic audit is the act of turning on the lights in a cluttered room. It replaces the chaos of assumption with the clarity of intention, empowering you not just to cut costs, but to build your future on a foundation you can finally see
Why Your “Gut Feeling” About SaaS Spend is Wrong
It seems to me that most mid-sized businesses are running on this deeply flawed assumption: We know what we use. Seriously? SaaS spend management isn’t a one-time event; it’s a living, breathing nightmare. I mean, my old firm once found a developer in Sacramento who had provisioned an obscure database tool; let’s call it ‘DB-Forge Pro 2.1’—for a two-week project back in 2018. They charged it to a ghost card, never used it again, and guess what? Four years later, it was still auto-renewing for $1,200 annually.
And that’s the benign part, isn’t it? The financial hemorrhage is one thing. But what about the security nightmare of orphaned accounts? If I had to bet, a lot of that hidden spend is directly linked to credentials that no one monitored, which is basically an open invitation for a breach.
And that’s the kicker. The resistance you’ll feel isn’t about the software. It’s about people’s workflows. Their habits. Their comfort zones.
Getting Started: What Exactly Are We Auditing?
So, you’ve decided to stop the bleeding. Good. But where do you start? It’s not just counting licenses; it’s a three-dimensional chess game involving finance, security, and usage. I’m probably wrong, but the biggest mistake people make is looking only at the accounting ledger. The ledger only shows what was paid for. It misses the shadow IT discovery, all the stuff individuals have signed up for with corporate cards or even personal cards that now touch corporate data. Seriously, you wouldn’t believe the things people connect to Slack.
Here’s the thing, you need to broaden your definition of a SaaS asset. It’s not just Salesforce or Microsoft 365. It includes that free project management tool, the obscure API subscription your marketing team uses, and yes, even that 10 font-licensing platform. Every single touchpoint is an attack surface.
Phase 1: The Discovery & Data Collection Sprint
This first phase has to be ruthless and comprehensive. Don’t be polite. Just gather the data.
The Financial Sweep: Understanding the ‘Paid’ Portfolio
You need to integrate your finance tools—AP (Accounts Payable), expense reports, bank statements—and look for recurring charges. Don’t just search “Adobe.” Search for every single charge under $50. That’s where the low-value, high-volume stuff hides. We’re doing a full SaaS Audit Checklist here, so no stone unturned.
Image Suggestion: A detailed, clean screenshot mockup of a finance dashboard highlighting suspicious or unusually low recurring charges over a 12-month period. Image Alt-Text: Finance dashboard view for SaaS Audit Checklist focusing on low-dollar recurring payments.
Unpacking the License Details
For every subscription you find, you need four key data points. And this is crucial.
- Contract/Renewal Date: When does it auto-renew? We need time to renegotiate.
- Per-User Cost & Tier: Are we paying for Premium features that no one uses?
- Owner/Stakeholder: Who is the person responsible for this tool? Not just the person who paid for it.
- Usage Data Access: Can we actually pull a report on who logged in last? If not, that’s a red flag right there.
The Security Sweep: Finding Shadow IT and Orphaned Access
This is where the risk lives. Shadow IT discovery is never easy, but it’s essential for a proactive SaaS audit. We’re talking about unapproved tools that somehow integrated with your core systems. But, so, how do you find them?
You have to look at logs. Seriously. Check the OAuth permissions granted to third-party apps by your core identity provider (like Okta or Azure AD). You’ll see things like “RandomPhotoEditor.io” having ‘Read/Write’ access to your employee directory. Jeepers.
Look for user accounts that are still active for former employees or contractors. It’s basic hygiene, but it gets forgotten, and those are the accounts that hackers love. They’re often high-privilege and low-monitoring. [Cite: Recent Industry Study on SaaS Adoption] suggests that 45% of breached SaaS environments involved dormant or orphaned accounts. It’s terrifying, but true.
Phase 2: Analysis & Strategic Intervention
Once the data is messy, raw, and comprehensive, we can start to clean it up. This part is about making hard choices and setting a governance framework.
Is This License Actually Being Used?
The core question in any software license audit is usage. Don’t just ask the department head. Ask the tool. Use the native admin dashboards to pull login data. Here’s a basic metric: if a user hasn’t logged in within 90 days, that license is basically dormant. Why are we paying for it?
And that’s the thing about SaaS license optimization: it means right-sizing, not just cutting. Maybe you have 100 licenses but only 50 are active. That’s 50 that need to go. But perhaps you have 10 users who desperately need the ‘Enterprise Reporting’ feature, but are stuck on the ‘Pro’ tier. That’s a good investment.
Consolidate, Contract, and Conquer
You’ll find overlap. Trust me. Two different teams using two different project management tools (Jira and Asana, maybe). Or five different services for e-signatures. This is where vendor consolidation comes in.
You need to pick the best-in-class tool and force the migration. It’s painful—I won’t lie—but it simplifies your training, your billing, and critically, your security posture. Fewer vendors mean fewer contracts to manage and fewer APIs to secure. It’s basic B2B SaaS optimization. We can’t forget that.
Then, there are the renewals. Set a 60-day flag for any major renewal date. Use that window for SaaS contract renegotiation. Seriously, armed with your actual usage data (the kind you just gathered), you have massive leverage. You can demand a price reduction or better terms if you’re only using 70% of the capacity you agreed to. This whole process is basically about making the vendors work for your money, for once. I guess that’s fair.
Prompt: A simple, illustrative Venn diagram where the overlapping center is labeled ‘The Optimized SaaS Stack,’ and the three outer circles are labeled ‘Security,’ ‘Usage,’ and ‘Cost.’ Image Alt-Text: Venn diagram showing the three goals of a SaaS Audit Checklist: security, usage, and cost.
Phase 3: The Governance Loop and Future-Proofing
The honest, slightly depressing truth? This is never over. You need a permanent governance loop. Otherwise, in six months, you’ll be doing the exact same SaaS audit checklist again.

Making It Official: The SaaS Procurement Policy
You need a policy that clearly states: No new SaaS tool, regardless of cost, can be adopted without approval from IT/Security and Finance. Full stop. No exceptions for that pesky, 10-a-month tool. That 10 tool usually asks for the most dangerous permissions.
And that’s the thing. The policy needs teeth. But it also needs a pathway. You can’t stifle innovation. The approval process should be clear, fast, and simple for low-risk, low-cost tools. But it should stop any high-cost or high-permission tool in its tracks until it’s been vetted.
This whole approach—the proactive SaaS audit—shifts the mentality from “fire-fighting spend” to “strategic technology management.” You’re not just saving money; you’re building resilience. And that’s what this is all about. Seriously. We’re in the B2B SaaS space, and security is the product, even if you’re selling something else entirely.
I’m probably wrong, but if you manage to formalize this process, you will immediately see a reduction in not only wasted licenses but also the noise in your security incident queue. The system will start policing itself. It seems to me that having an annual review, maybe in September—our old firm used to do it then because it was far from the fiscal year-end rush—is perfect for resetting and looking ahead.
We’re not looking for perfect compliance, mind you. We’re looking for control. This isn’t about micromanaging every developer’s choice of sticky-note app. It’s about ensuring the big, data-touching, mission-critical apps are fully vetted, optimally licensed, and decommissioned the moment they stop providing value. And that, I guess, is a solid win.

Leave a Reply